Compromise Assessments Services
Compromise Assessments Services
In an increasingly hostile cyber landscape, identifying and mitigating unauthorized intrusions is critical for protecting your organization’s sensitive data and maintaining operational integrity. Our Compromise Assessments Services are designed to determine whether your organization has been compromised by cyber threats, with a particular focus on detecting hidden breaches that may have evaded traditional security measures. Leveraging advanced technologies and expert analysis, we help you uncover and address security incidents swiftly and effectively, ensuring your business remains secure and resilient against evolving threats.
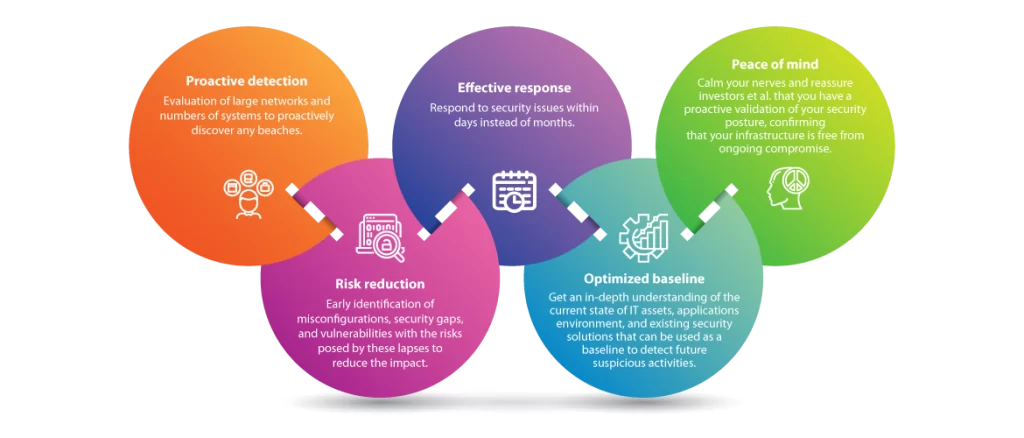
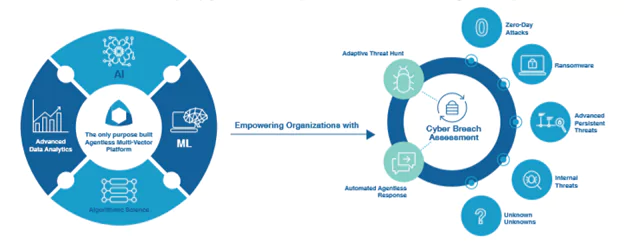
Our Compromise Assessments Services provide a thorough investigation into your organization’s IT infrastructure to identify signs of unauthorized access, data breaches, and other malicious activities. Whether you suspect a security incident or seek to validate the integrity of your systems proactively, our services deliver the insights and actions necessary to detect hidden breaches and restore your security posture. We combine state-of-the-art forensic techniques, threat intelligence, and experienced cybersecurity professionals to offer comprehensive assessments tailored to your specific needs.

Comprehensive Security Evaluation:
- System and Network Analysis: Examine your entire IT environment, including servers, workstations, network devices, and cloud infrastructures, to identify anomalies and potential indicators of compromise.
- Log Review and Correlation: Analyze system logs, network traffic, and security alerts to detect suspicious activities and patterns indicative of unauthorized access.
Advanced Threat Detection:
- Behavioral Analysis: Utilize behavioral analytics to identify deviations from normal operations that may signal a compromise.
- Malware and Rootkit Detection: Employ specialized tools to uncover malicious software and rootkits that could be concealing unauthorized activities.
Forensic Investigation:
- Data Collection and Preservation: Securely collect and preserve digital evidence to ensure the integrity and admissibility of findings.
- Incident Reconstruction: Reconstruct the sequence of events leading to the compromise to understand the attack vectors and methodologies used by adversaries.
Vulnerability Identification:
- Weakness Assessment: Identify vulnerabilities in your systems and applications that could have been exploited by attackers.
- Exploit Analysis: Analyze known exploits and their impact on your environment to assess the extent of potential damage.
Remediation and Recovery:
- Actionable Recommendations: Provide clear and prioritized recommendations to remediate identified vulnerabilities and strengthen your security defenses.
- Recovery Planning: Assist in developing and implementing recovery strategies to restore affected systems and minimize downtime.
Reporting and Documentation:
- Detailed Findings Report: Deliver comprehensive reports outlining detected compromises, evidence collected, analysis performed, and remediation steps.
- Executive Summaries: Provide high-level summaries for senior management to facilitate informed decision-making and strategic planning.
Continuous Monitoring Integration:
- Enhanced Detection Capabilities: Recommend and integrate continuous monitoring solutions to improve your ability to detect and respond to future compromises swiftly.
- Threat Intelligence Sharing: Incorporate up-to-date threat intelligence to stay ahead of emerging cyber threats and tactics.
Training and Awareness:
- Incident Response Training: Train your staff on effective incident response procedures to enhance your organization’s ability to handle future security incidents.
- Security Best Practices: Educate employees on best practices for maintaining a secure environment and recognizing potential threats.
-
- Enhanced Security Posture:
-
- Proactive Threat Mitigation: Identify and address compromises early, preventing further damage and reducing the overall risk to your organization.
- Comprehensive Protection: Strengthen your defenses by uncovering and resolving hidden vulnerabilities and unauthorized access points.
Regulatory Compliance:
-
- Meet Legal Requirements: Ensure compliance with data protection and cybersecurity regulations by thoroughly investigating and addressing security incidents.
- Audit Readiness: Maintain detailed documentation and evidence to support regulatory audits and compliance reviews.
Operational Continuity:
-
- Minimized Downtime: Quickly identify and remediate compromises to restore normal operations and minimize business disruptions.
- Robust Recovery Plans: Develop effective recovery strategies to ensure business continuity in the face of cyber incidents.
Cost Efficiency:
-
- Reduced Remediation Costs: Addressing compromises promptly reduces the financial impact associated with prolonged breaches and data loss.
- Preventative Savings: Implementing recommended security measures helps prevent future incidents, saving costs related to breach remediation and reputation management.
Increased Trust and Confidence:
-
- Build Credibility: Demonstrate your commitment to cybersecurity by proactively identifying and addressing compromises, fostering trust with customers and stakeholders.
- Competitive Advantage: Differentiate your organization by showcasing robust security practices and a proactive approach to threat management.
-
- Enhanced Security Posture:

Use Cases:
- Financial Institutions:
- Protect sensitive financial data and transactions, ensuring compliance with industry-specific cybersecurity regulations and safeguarding customer trust.
- Healthcare Organizations:
- Safeguard patient information and medical records, complying with healthcare data protection laws and preventing unauthorized access to sensitive data.
- Government Agencies:
- Secure classified and sensitive government data, maintaining national security and public trust through rigorous compromise assessments.
- E-Commerce Platforms:
- Ensure the security of customer data and transaction information, enhancing trust and reducing the risk of data breaches in online operations.
- Telecommunications Companies:
- Protect communication networks and customer data, maintaining reliable and trusted service delivery through comprehensive security assessments.
- Educational Institutions:
- Safeguard academic records and personal information of students and staff, ensuring compliance with data protection standards and preventing unauthorized access.
- Manufacturing Firms:
- Protect intellectual property and operational technologies from cyber threats, ensuring business continuity and maintaining competitive advantage.
- Retailers and Merchants:
- Secure point-of-sale (POS) systems and customer data to prevent data breaches, ensuring compliance with privacy laws and maintaining customer trust.
