Red Team
Red Team
In the realm of information security, a red team comprises ethical hackers proficient in evaluating an organization’s defensive measures by emulating genuine cyber threats within a controlled setting. These seasoned professionals meticulously craft the conditions necessary for comprehensive assessments, establishing clear objectives and deploying appropriate tools to facilitate their rigorous evaluations. With a focus on teamwork and expertise, they navigate the complexities of simulated attacks to effectively fulfill their demanding responsibilities.
Red teaming, also known as red team security testing, epitomizes ethical hacking practices employed by an independent security unit to uncover vulnerabilities and gauge risks across an organization’s infrastructure. This multifaceted approach extends beyond assessing technical systems to include scrutinizing human factors and physical environments. Through the enactment of diverse attack scenarios, from social engineering ploys to sophisticated penetration techniques, red teams provide invaluable insights into an organization’s susceptibility to real-world threats. Armed with reconnaissance data, they strategically map out attack vectors and develop tailored strategies to expose weaknesses, ensuring a thorough evaluation of the organization’s security posture.

Red teaming is a proactive cybersecurity evaluation strategy that involves assessing an organization’s defenses from an adversarial perspective, thus eliminating any inherent defender bias. Ethical hackers, authorized by the organization, mimic real attackers to thoroughly evaluate its systems. By employing attack simulation methodologies, these specialists replicate the tactics, techniques, and procedures utilized by sophisticated attackers or advanced persistent threats. This comprehensive approach not only identifies technical weaknesses but also assesses the resilience of the organization’s people, processes, and technologies against specific attack objectives.
This process serves as a proactive security risk assessment service, enabling organizations to effectively identify and address IT security gaps and weaknesses. Unlike vulnerability assessments and penetration testing, which focus solely on uncovering known technical weaknesses, red team exercises provide actionable insights into the overall state of an organization’s IT security posture. Through red teaming, organizations gain valuable insights into their cybersecurity readiness and can take proactive measures to enhance their defenses and mitigate potential threats effectively.
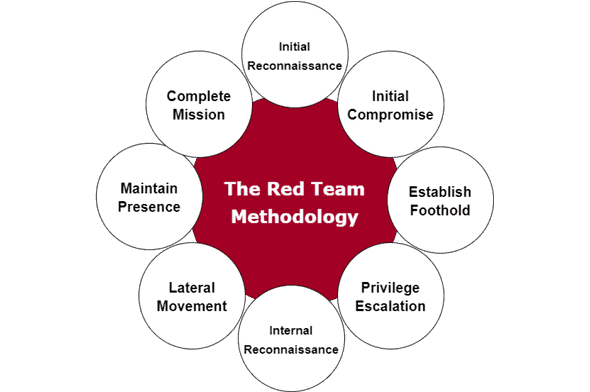
In-Depth Assessments: We simulate real-world cyber attacks to identify vulnerabilities across your organization.
Realistic Attack Simulation: Our team mimics actual threat actor tactics to evaluate your defenses.
Proactive Reconnaissance: We gather critical information about your network before assessments.
Actionable Insights: Receive detailed reports with findings and recommendations for security improvements.
Ongoing Support: We assist with implementing security enhancements post-assessment.
Choose SalekX for tailored cybersecurity solutions that enhance your organization’s resilience.
