Social Engineering Assessments Services
Social Engineering Assessments Services
In today’s interconnected world, human factors play a critical role in the security posture of any organization. Cybercriminals increasingly exploit human vulnerabilities through social engineering attacks, such as phishing, pretexting, and baiting, to gain unauthorized access to sensitive information and systems. Our Social Engineering Assessments Services are meticulously designed to evaluate and enhance your organization’s resilience against these sophisticated tactics. By testing the susceptibility of your employees and reinforcing security awareness, we help you safeguard your critical assets and maintain a robust defense against social engineering threats.
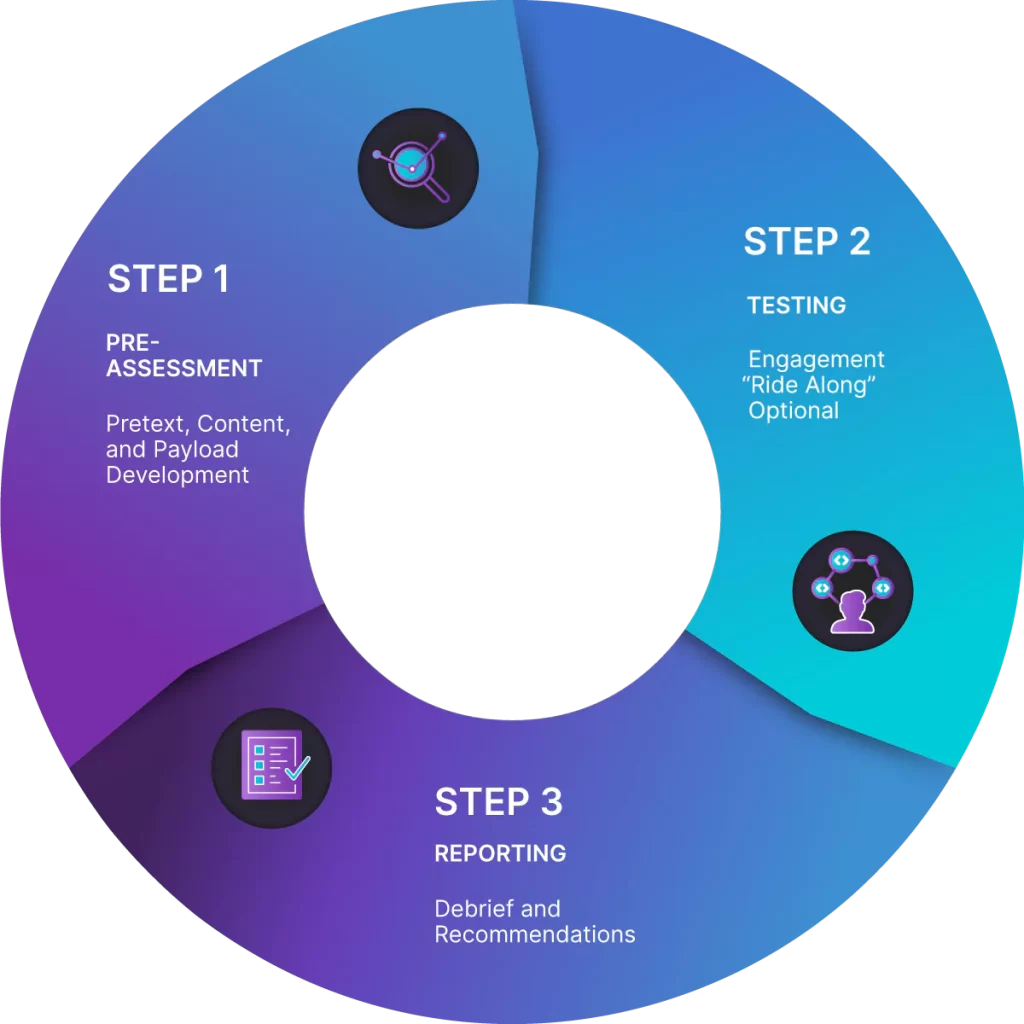
Our Social Engineering Assessments Services provide a comprehensive evaluation of your organization’s vulnerability to social engineering attacks. We simulate real-world scenarios to assess how well your employees can recognize and respond to various social engineering techniques. By identifying weaknesses in human defenses, we enable you to implement targeted training and security measures that strengthen your overall security posture. Whether you aim to enhance employee awareness, comply with regulatory requirements, or prevent costly security breaches, our social engineering assessments offer the insights and strategies necessary to protect your organization from manipulation and deception.
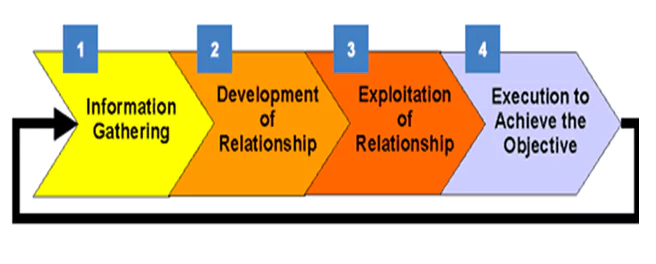
- Simulated Phishing Attacks:
- Email Phishing Simulations: Conduct realistic phishing campaigns to assess employees’ ability to identify and respond to deceptive emails.
- Spear Phishing Tests: Target specific individuals or departments with tailored phishing attempts to evaluate the effectiveness of your organization’s defenses against personalized attacks.
- Pretexting and Impersonation Tests:
- Telephone Pretexting: Simulate phone-based social engineering attempts to assess employees’ vigilance and adherence to verification protocols.
- In-Person Impersonation: Conduct on-site tests where assessors pose as trusted individuals to evaluate physical security measures and employee responses.
- Vishing and Smishing Simulations:
- Vishing (Voice Phishing): Simulate voice-based attacks to assess employees’ ability to recognize and respond to fraudulent phone calls.
- Smishing (SMS Phishing): Test the susceptibility of employees to text message-based phishing attempts, ensuring awareness of mobile security threats.
- Baiting and Tailgating Exercises:
- Baiting Scenarios: Implement baiting techniques, such as leaving infected USB drives, to evaluate employees’ response to unsolicited physical media.
- Tailgating Assessments: Test the effectiveness of access control measures by attempting unauthorized entry alongside authorized personnel.
- Security Awareness Training:
- Customized Training Programs: Develop and deliver targeted training sessions based on assessment findings to educate employees on recognizing and mitigating social engineering threats.
- Interactive Workshops: Engage employees with interactive workshops and role-playing exercises to reinforce security best practices and improve response strategies.
- Reporting and Analysis:
- Detailed Assessment Reports: Provide comprehensive reports outlining the results of social engineering simulations, highlighting vulnerabilities and areas for improvement.
- Behavioral Analysis: Analyze employee behaviors and responses to identify patterns and trends that inform future training and security measures.
- Remediation Recommendations:
- Actionable Insights: Offer clear and practical recommendations to address identified weaknesses and enhance your organization’s defenses against social engineering attacks.

- Enhanced Employee Awareness:
- Proactive Defense: Equip your employees with the knowledge and skills to recognize and respond to social engineering threats effectively.
- Culture of Security: Foster a security-conscious culture where employees understand their role in maintaining organizational security.
- Reduced Risk of Data Breaches:
- Minimized Vulnerabilities: Identify and address human-related vulnerabilities before they can be exploited by malicious actors.
- Cost Savings: Prevent costly data breaches and the associated financial and reputational damage through effective risk mitigation.
- Regulatory Compliance:
- Meet Legal Requirements: Ensure compliance with data protection and cybersecurity regulations that mandate employee training and security awareness.
- Audit Readiness: Maintain thorough documentation of social engineering assessments and training initiatives to support regulatory audits and compliance reviews.
- Increased Organizational Resilience:
- Robust Security Posture: Strengthen your organization’s overall security posture by integrating human defenses with technical safeguards.
- Adaptability: Enhance your ability to adapt to evolving social engineering tactics and emerging cyber threats.
- Customer Trust and Confidence:
- Build Credibility: Demonstrate your commitment to cybersecurity, fostering trust and confidence among customers, partners, and stakeholders.
- Competitive Advantage: Differentiate your organization by showcasing superior security awareness and proactive defense measures.
Use Cases:
- Financial Institutions:
- Protect sensitive financial data and customer information by ensuring employees can identify and thwart sophisticated social engineering attacks.
- Healthcare Organizations:
- Safeguard patient information and medical records by reinforcing employee awareness of privacy and security best practices.
- Government Agencies:
- Secure classified and sensitive government data by testing and improving employee defenses against social engineering threats.
- E-Commerce Platforms:
- Enhance customer trust by ensuring your workforce can recognize and prevent social engineering attempts aimed at compromising transaction data.
- Telecommunications Companies:
- Protect communication networks and customer data by assessing and improving employee resistance to social engineering tactics.
- Educational Institutions:
- Safeguard academic records and personal information of students and staff by promoting a culture of security awareness and vigilance.
- Manufacturing Firms:
- Protect intellectual property and operational technologies by ensuring employees can recognize and respond to social engineering threats.
- Retailers and Merchants:
- Secure point-of-sale (POS) systems and customer data by reinforcing employee defenses against social engineering attacks.
